Securing your Wordpress website is critical for protecting your sensitive information and maintaining your user trust. This guide offers detailed strategies based on industry best practices to help protect your website.
Secure Hosting Environment
A secure hosting environment is the foundation of your website’s security. Here are key measures to consider:
Web Penetration Testing
An important step that involves a security assessment simulating attacks to find vulnerabilities. It is essential to conduct these tests before launching your site and at least once a year afterward. This process helps identify weaknesses and offers insights for fixing them.
Secure Hosting
Consider using VPS or dedicated hosting, as these offer better security than shared hosting. Managed WordPress Hosting is also a good choice because it often includes built-in security features, daily backups, and automatic updates.
Many companies prefer to host multiple websites under one cPanel or Plesk account. However, if one website gets hacked, it can put all the sites in that account at risk. This can lead to the entire hosting account being compromised.
Common Misconceptions: Some believe services like AWS or GCP are secure. In reality, improper management are the core to lead to vulnerabilities.
You can verify the cPanel/WHM license by using your website (server)’s IP address @ cPanel/WHM License Verification
Implement SSL Certificates
SSL certificates encrypt data between users and your server, protecting sensitive information from interception. Additionally, secured sites are favored by search engines, which can improve your site’s ranking.
Firewall Implementation
Implementing advanced firewall services is another effective strategy. Tools like Cloudflare, BitNinja or Imunify360 can block malicious traffic before it reaches your server and protect against DDoS attacks.
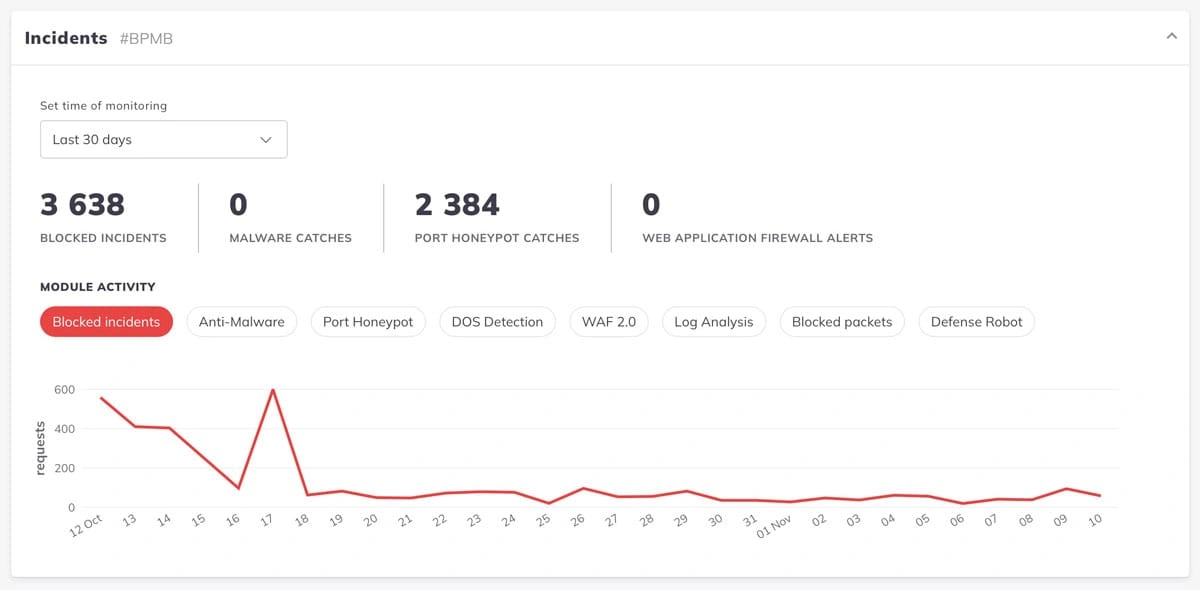
If you are using Cloudflare, you may follow this awesome guide Cloudflare WAF Rules V3 by Troy Glanc.
Content Security Policy Header (CSP)
Setting up a content security policy (CSP) is also crucial. CSP headers help prevent XSS attacks by defining trusted sources for loading scripts and resources. You can implement a CSP that limits the domains allowed to load content on your site, reducing the risk of code injection.
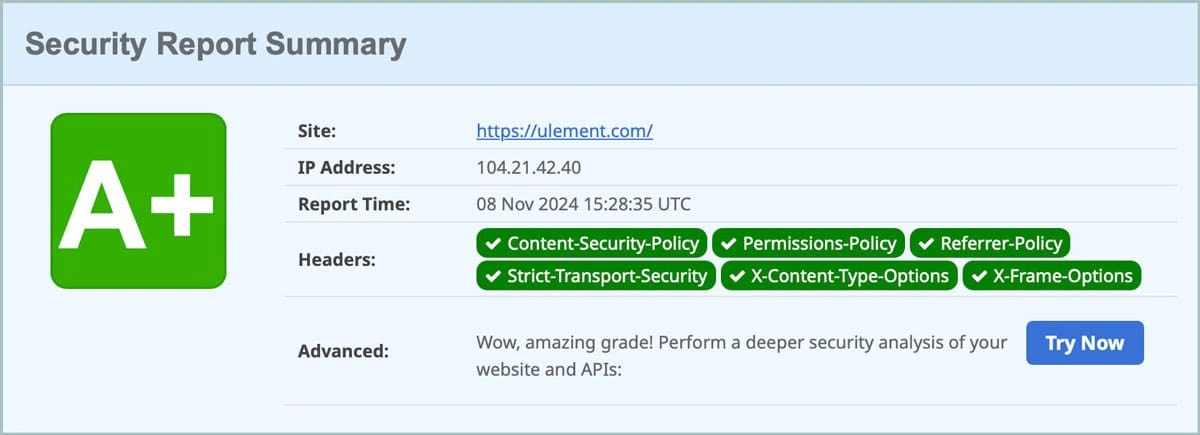
You may check your security header @ securityheaders.com
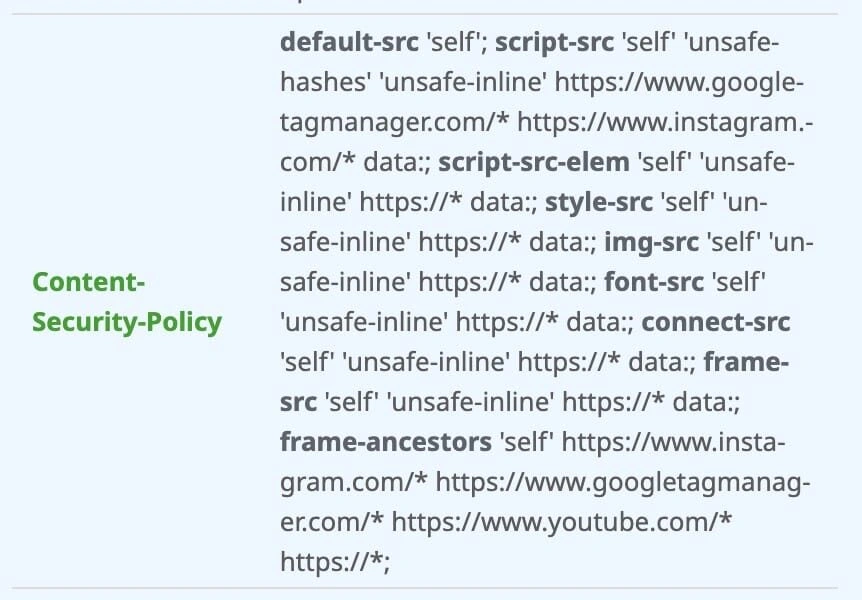
This is a poorly configured setup by a well-known digital agency. They are using https://* in the client’s website Content Security Policy, which undermines the purpose of implementing a security header. This approach allows resources to be loaded from any HTTPS domain, effectively negating the security benefits of CSP.
HTTP Strict Transport Security Header (HSTS)
Using HTTP Strict Transport Security (HSTS) ensures secure communications between the user’s browser and your server. This measure prevents man-in-the-middle attacks by enforcing secure connections.
Secure File Transfer
For file transfers, use SFTP or SSH. These protocols encrypt data transferred between your machine and the server, keeping it secure from interception.
Close Unused Ports
Auditing your server to identify and close any unused ports is also essential. This minimizes entry points for attackers and reduces the risk of unauthorized access.
Server Logging
Maintaining detailed server logs is important for monitoring and tracking suspicious activities. Regularly reviewing these logs helps identify unusual patterns or unauthorized access attempts.
Robust Backup Strategy
comprehensive backup plan is essential for data protection. Store backups securely off-site to avoid data loss and automate backups at regular intervals. It is also important to test the restoration to ensure recovery works smoothly.
Our backup strategy is server’s backups at daily intervals for 14 days. Website backups up to 60 days. This dual approach helps to safeguard the data effectively, providing a reliable safety net in case of any unexpected issues or data loss.
User Management
Proper user management is crucial for maintaining security on your WordPress site.
Strong Password Policies
Enforcing strong password policies will require users to create complex passwords that include uppercase letters, lowercase letters, numbers, and special characters. Implementing a password expiry policy that requires changes every 90 days and disallows the reuse of old passwords enhances security further. Please consider using a password manager to help generate and store secure passwords.

Maintain STRONG password habits across all your platforms. I have a client who lost his Facebook page, Google My Business, and YouTube account because of the in-house web developer’s lack of security knowledge. Over a year, several of their websites faced security issues, and someone accessed even his CloudFlare account, changed the A records settings and the account password. Fortunately, we are managing these websites, and we could resolve the issues in less than a day.
And thanks to him, I get the idea to write this post and present at WordCamp Malaysia.
Two-Factor Authentication (2FA)
Enable 2FA adds an extra layer of security by requiring a second verification step, such as a text code or authentication app. Enabling 2FA for all accounts, especially those with administrative access, is highly recommended.
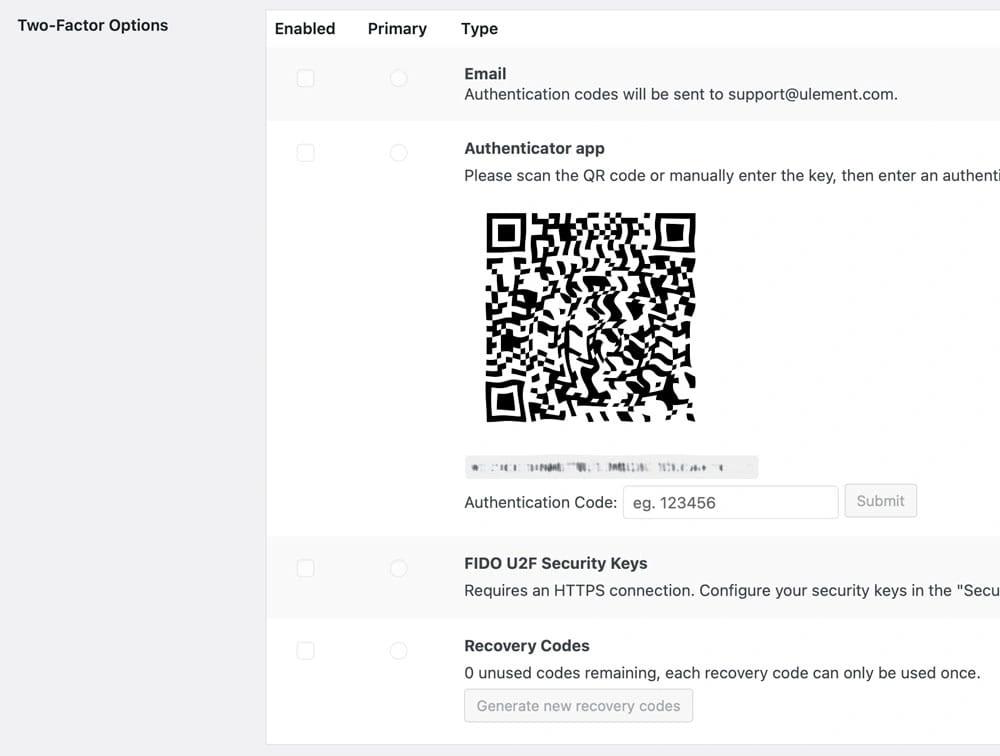
Login Whitelisting
This is particularly effective for accounts where access should be limited to known locations.
Account Management
Review and remove unnecessary administrative accounts to limit potential security risks.
Stronger Password Hashing
Using a strong password hashing algorithm like bcrypt hashing is critical as it makes it difficult for attackers to crack hashed passwords using brute-force methods.
User Activity Logging
Implement detailed logging of user activities to help track and investigate suspicious actions effectively. Monitor changes made by users, especially those with administrative privileges, to quickly identify unauthorized modifications.
Plugin and Theme Management
Plugins and themes can introduce vulnerabilities if not managed properly.
Official Sources Only
When managing plugins and themes, always download them from official WordPress repositories or original developers. DO NOT use nulled themes or plugins that may contain malicious code or backdoors that could compromise your site’s security.
Regular Updates
Keep all themes and plugins up-to-date with the latest security patches protects against vulnerabilities.
Minimize Vulnerabilities
Regularly audit your site to remove unused themes and plugins promptly, as each inactive component can serve as a potential entry point for attackers.
Daily Vulnerability Scanning
Implement daily vulnerability scanning tools like Malcare or PatchStack provides comprehensive security monitoring. Daily scans help detect threats early, allowing for prompt updates to protect against new vulnerabilities.
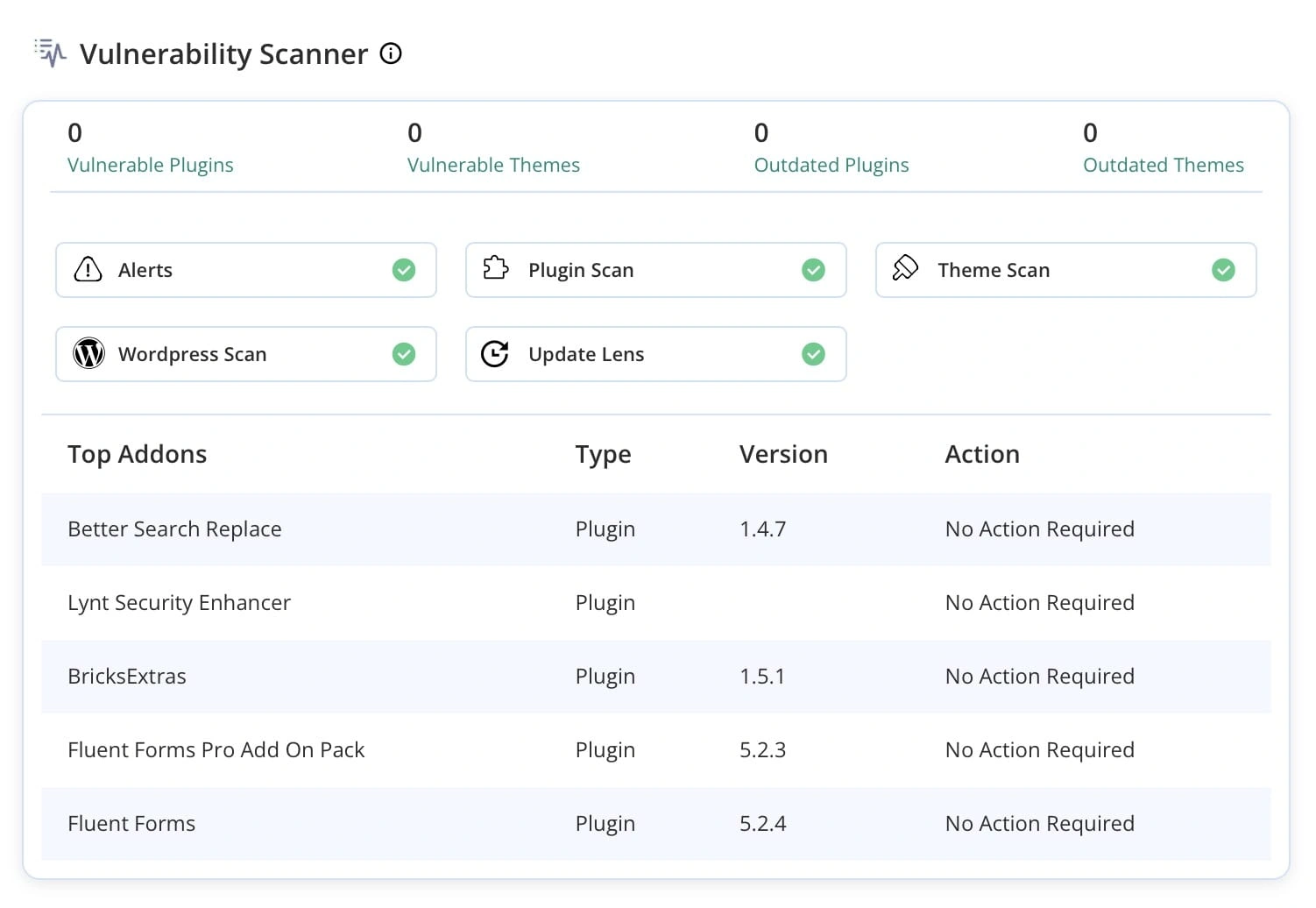
Improve WordPress Security
Beyond basic measures, there are additional steps you can take to enhance your site’s security. Before adding any code, it is highly recommended that you make a copy prior to implementation.
Auto Minor Core Update
Enable automatic minor core updates, which include maintenance and security updates. Add the following code to your wp-config.php:
define( 'WP_AUTO_UPDATE_CORE', minor ); Disable PHP Execution
Disabling PHP execution in directories where it is not needed can prevent malicious scripts from running. Add the following code to your .htaccess file:
<FilesMatch "\.+(?i:php|phtm)$"> deny from all </FilesMatch>Disable File Editing
Disabling the built-in file editor in WordPress settings helps prevent code injection exploits. Add the following code to your wp-config.php:
define('DISALLOW_FILE_EDIT', true);Disable Directory Browsing
Enhance security by preventing unauthorized users from viewing file structures and accessing sensitive information on the server. Add the following code to your .htaccess file:
Options -IndexesLimit XML-RPC Usage
If XML-RPC is not needed for your site’s functionality (e.g., remote publishing), disable it to mitigate brute-force attacks that can exploit xmlrpc.php. Add the following code to your .htaccess file:
<Files xmlrpc.php>
Order Deny,Allow
Deny from all
</Files>Restrict REST API Access
Restricting REST API access for non-administrative users minimizes potential information leaks that could be exploited.
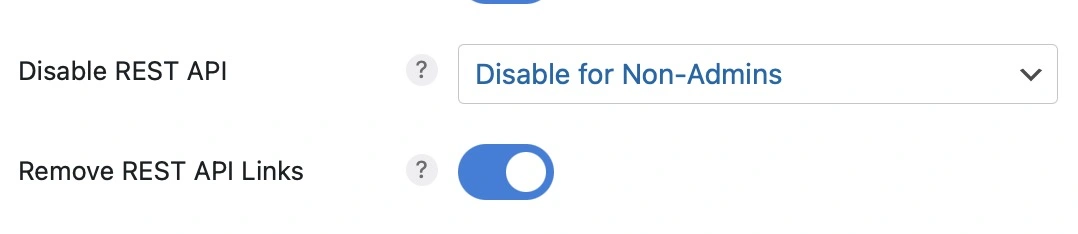
Or use code snippet (from Disable REST API without Plugins)
add_filter( 'rest_authentication_errors', 'rudr_turn_off_rest_api_not_logged_in' );
function rudr_turn_off_rest_api_not_logged_in( $errors ) {
// if there is already an error, just return it
if( is_wp_error( $errors ) ) {
return $errors;
}
if( ! current_user_can( 'administrator' ) ) {
// disable REST API for everyone except administrators
return new WP_Error( 'no_rest_api_sorry', 'REST API not allowed', array( 'status' => 401 ) );
}
return $errors;
}Noindex Search Results
Prevent SEO spam by adding noindex tags to search results, coupled with implementing a CSP header and disabling PHP execution where unnecessary. Add the following code to your robots.txt file:
User-agent: *
Disallow: /?s=
Disallow: /page/*/?s=
Disallow: /search/Government websites getting hacked?
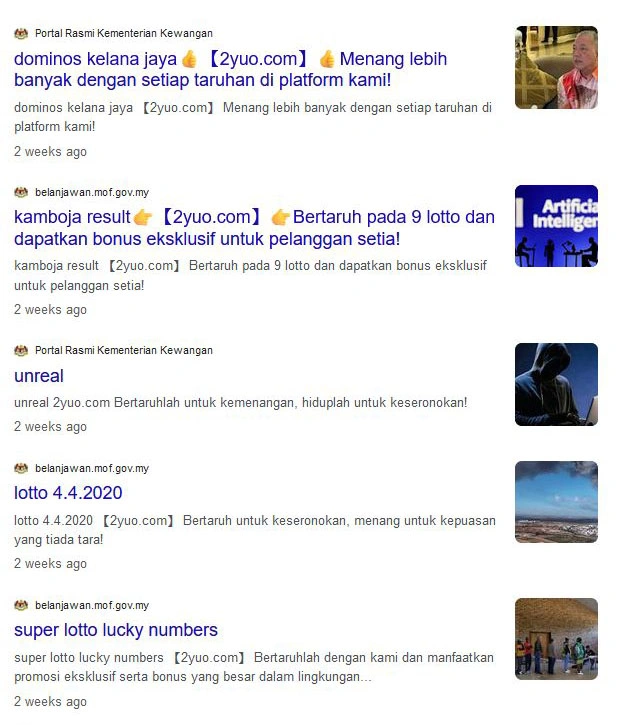
This issue is caused by lack of security knowledge. Search results shouldn’t be indexed, and the website’s content security policy header is missing. If they have conducted any web penetration tests, the missing of security header will definitely be marked as a risk that needs to be addressed.
Education and Awareness
Educating your client on security best practices is crucial for maintaining a secure environment.
Conduct Regular Security Training Sessions
Educating clients about security best practices is essential for maintaining a secure environment. Conducting ongoing training sessions will help client recognize phishing attempts and maintain strong passwords.
Developing Clear Incident Response Plans
Outlining roles during a breach will prepare your team for potential threats.
Conclusion
Enhance WordPress security by regularly updating software, using strong passwords, and installing reputable security plugins. Secure your login page, limit login attempts, and enable two-factor authentication. Frequent backups and a reliable hosting provider further safeguard your site.
In our case studyies, most of the security issues arise from human error, such as weak passwords or the use of nulled themes/plugins. By implementing these security measures and educating your team/client about security practices is very important.
FAQs
What is the first step in securing my WordPress website?
Start with a secure hosting environment that offers better isolation and enhanced security features.
Consider downloading the presentation shared at WordCamp Malaysia 2024 for a simplified overview of these strategies.
Secure Your WordPress Site with Expert Maintenance!
If you need someone for strong security and support for your WordPress site, choose our expert Maintenance & Support services.